Download DualShield IdP certificate
- Login into DualShield console, select "SSO".
- Click the SSO Server's context menu, select "Download IdP Certificate".
![DualShield MFA Platform > ASA Configuration [ASAM] > worddav197c5df8ffefa1c65756ba9c953e5751.png](/download/attachments/35946775/worddav197c5df8ffefa1c65756ba9c953e5751.png?version=1&modificationDate=1587385454000&api=v2)
Upload DualShield IdP certificate
The DualShield IdP certificate that we downloaded in the last step needs to be uploaded onto the Cisco ASA
- Launch Cisco ASDM
- Navigate to "Remote Access VPN | Certificate Management| CA certificate"
- Click "Add", enter "Name" and install the earlier downloaded IdP certificate
![DualShield MFA Platform > ASA Configuration [ASAM] > worddavac21cfa997c3cbb0b7a4cf2a4c2de9b9.png](/download/attachments/35946775/worddavac21cfa997c3cbb0b7a4cf2a4c2de9b9.png?version=1&modificationDate=1587385454000&api=v2)
Create Cisco SP certificate
In SAML authentication, Cisco ASA is a so-called Service Provider (SP), and it needs a SSL server certificate. You can ask ASA to create a self-signed certificate.
- Launch Cisco ASDM
- Navigate to "Remote Access VPN | Certificate Management| Identity Certificates"
- Click "Add"
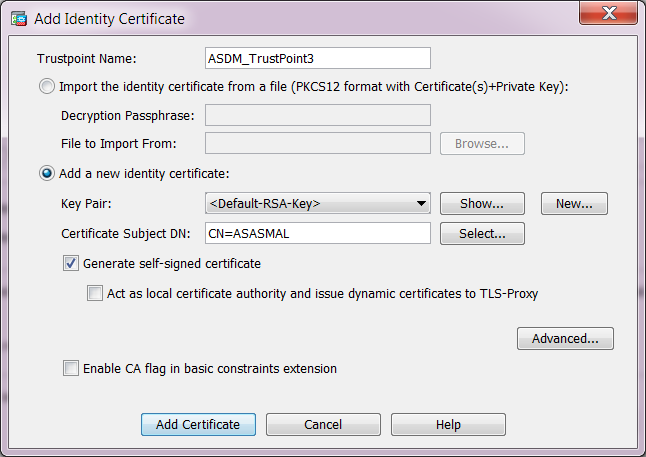
- Select the option: "Add a new identity certificate"
- Tick "Generate self-signed certificate"
- Click "Add Certificate"
Extract DualShield IdP metadata
- Login into DualShield console, select "SSO".
- Click the SSO Server's context menu, select "View".
![DualShield MFA Platform > ASA Configuration [ASAM] > image2019-4-4_15-34-56.png](/download/attachments/35946775/image2019-4-4_15-34-56.png?version=1&modificationDate=1587385454000&api=v2)
Make note of "entityID", "Login URL" and "Logout URL" as highlighted above.
Modify "Connection Profiles" in ASA
- Launch Cisco ASDM
- Navigate to "Remote Access VPN | Clientless SSL VPN Access | Connection Profiles"
![DualShield MFA Platform > ASA Configuration [ASAM] > worddav3ac61808b030690c74976ff2788680ff.png](/download/attachments/35946775/worddav3ac61808b030690c74976ff2788680ff.png?version=1&modificationDate=1587385454000&api=v2)
- Click "Add" in "Connection Profiles" panel
![DualShield MFA Platform > ASA Configuration [ASAM] > worddav81f59c4305ee3f09b5304130ca8ab9fd.png](/download/attachments/35946775/worddav81f59c4305ee3f09b5304130ca8ab9fd.png?version=1&modificationDate=1587385454000&api=v2)
- Enter "Name" , "Aliases"
- In "Authentication – Method", select "SAML"
- Enable "Enable clientless SSL VPN protocol"
- Click the "Manage…" button
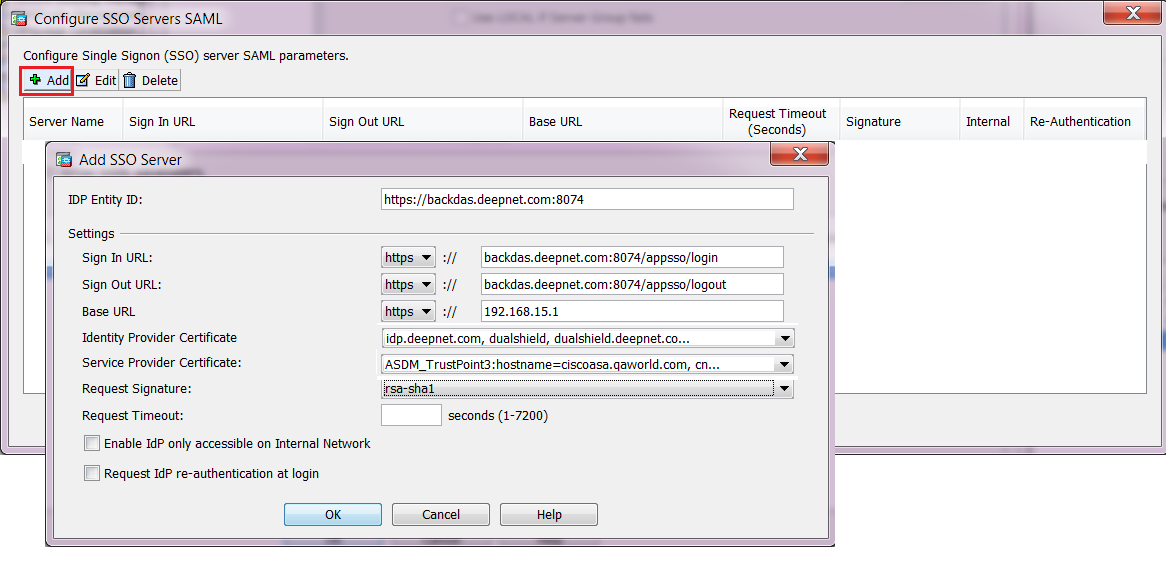
- Click "Add"
- Enter the "IdP Entity ID" , "Sign in URL" & "Sign out URL" which were found in previous steps.
- Select the correct "Identity Provider Certificate"
- Select the correct "Service Provider Certificate"
- Select "rsa-sha1" in "Request Signature" drop down list.
- Click "OK"
![DualShield MFA Platform > ASA Configuration [ASAM] > asa1.png](/download/attachments/35946775/asa1.png?version=1&modificationDate=1587385454000&api=v2)
- Click "Apply" to save the configuration.
Download Cisco SP metadata
Launch a web browser, navigate to https://[ASA-FQDN]/saml/sp/metadata/[saml vpn connection profile name], i.e. https://192.168.15.1/saml/sp/metadata/samlvpn.
![DualShield MFA Platform > ASA Configuration [ASAM] > asa2.png](/download/attachments/35946775/asa2.png?version=1&modificationDate=1587385454000&api=v2)
Save the metadata displayed in the browser as a text file, then open the file in a text editor, e.g. notepad
![DualShield MFA Platform > ASA Configuration [ASAM] > asa3.png](/download/attachments/35946775/asa3.png?version=1&modificationDate=1587385454000&api=v2)
In the URLs highlighted above, replace the “+” letter with the string “%2b”
Save the file.
![DualShield MFA Platform > ASA Configuration [ASAM] > worddav197c5df8ffefa1c65756ba9c953e5751.png](/download/attachments/35946775/worddav197c5df8ffefa1c65756ba9c953e5751.png?version=1&modificationDate=1587385454000&api=v2)
![DualShield MFA Platform > ASA Configuration [ASAM] > worddavac21cfa997c3cbb0b7a4cf2a4c2de9b9.png](/download/attachments/35946775/worddavac21cfa997c3cbb0b7a4cf2a4c2de9b9.png?version=1&modificationDate=1587385454000&api=v2)
![DualShield MFA Platform > ASA Configuration [ASAM] > image2019-4-4_15-34-56.png](/download/attachments/35946775/image2019-4-4_15-34-56.png?version=1&modificationDate=1587385454000&api=v2)
![DualShield MFA Platform > ASA Configuration [ASAM] > worddav3ac61808b030690c74976ff2788680ff.png](/download/attachments/35946775/worddav3ac61808b030690c74976ff2788680ff.png?version=1&modificationDate=1587385454000&api=v2)
![DualShield MFA Platform > ASA Configuration [ASAM] > worddav81f59c4305ee3f09b5304130ca8ab9fd.png](/download/attachments/35946775/worddav81f59c4305ee3f09b5304130ca8ab9fd.png?version=1&modificationDate=1587385454000&api=v2)
![DualShield MFA Platform > ASA Configuration [ASAM] > asa1.png](/download/attachments/35946775/asa1.png?version=1&modificationDate=1587385454000&api=v2)
![DualShield MFA Platform > ASA Configuration [ASAM] > asa2.png](/download/attachments/35946775/asa2.png?version=1&modificationDate=1587385454000&api=v2)
![DualShield MFA Platform > ASA Configuration [ASAM] > asa3.png](/download/attachments/35946775/asa3.png?version=1&modificationDate=1587385454000&api=v2)