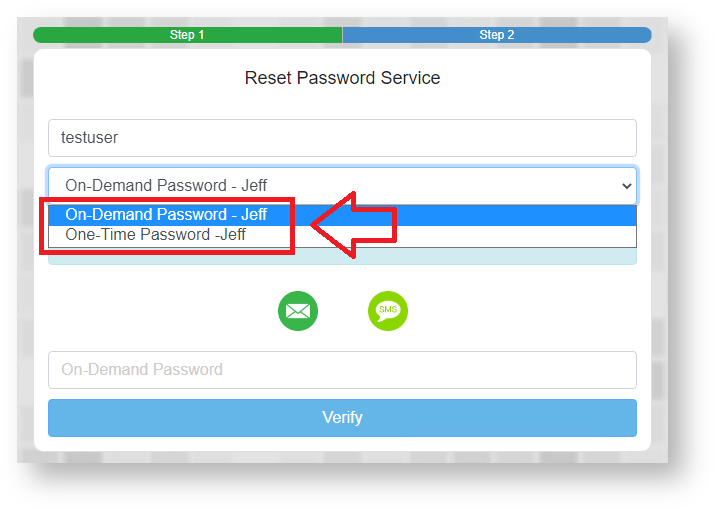
...
If we now log in to a protected application we will now see the above changes have also customised we can see that the names of the authentication methods displayed during authentication have also been customised;
It is worth pointing out that customisations made using this technique may be undone with future update of the authentication server software so it is advisable both to make backups of the affected files prior to any customisations, and to make notes on what customisations were made (so they can be re-implemented on updated versions if necessary).